Download Microsoft Security Operations Analyst.SC-200.ExamTopics.2026-02-18.220q.tqb
| Vendor: | Microsoft |
| Exam Code: | SC-200 |
| Exam Name: | Microsoft Security Operations Analyst |
| Date: | Feb 18, 2026 |
| File Size: | 10 MB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
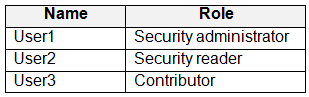
You have an Azure subscription that contains the users shown in the following table.
You need to delegate the following tasks:
- Enable Microsoft Defender for Servers on virtual machines.
- Review security recommendations and enable server vulnerability scans.
The solution must use the principle of least privilege.
Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 2
Your company has an on-premises network that uses Microsoft Defender for Identity.
The Microsoft Secure Score for the company includes a security assessment associated with unsecure Kerberos delegation.
You need remediate the security risk.
What should you do?
- Disable legacy protocols on the computers listed as exposed entities.
- Enforce LDAP signing on the computers listed as exposed entities.
- Modify the properties of the computer objects listed as exposed entities.
- Install the Local Administrator Password Solution (LAPS) extension on the computers listed as exposed entities.
Correct answer: C
Explanation:
C: 23 - Mosted C: 23 - Mosted
Question 3
You have a Microsoft 365 E5 subscription that uses Microsoft 365 Defender.
You need to review new attack techniques discovered by Microsoft and identify vulnerable resources in the subscription. The solution must minimize administrative effort.
Which blade should you use in the Microsoft 365 Defender portal?
- Advanced hunting
- Threat analytics
- Incidents & alerts
- Learning hub
Correct answer: B
Explanation:
B: 8 - Mosted B: 8 - Mosted
Question 4
You have an Azure subscription that uses Microsoft Defender for Cloud.
You have an Amazon Web Services (AWS) account that contains an Amazon Elastic Compute Cloud (EC2) instance named EC2-1.
You need to onboard EC2-1 to Defender for Cloud.
What should you install on EC2-1?
- the Log Analytics agent
- the Azure Connected Machine agent
- the unified Microsoft Defender for Endpoint solution package
- Microsoft Monitoring Agent
Correct answer: B
Explanation:
A: 7B: 30 - Mosted A: 7B: 30 - Mosted
Question 5
You have a Microsoft Sentinel workspace named Workspace1.
You configure Workspace1 to collect DNS events and deploy the Advanced Security Information Model (ASIM) unifying parser for the DNS schema.
You need to query the ASIM DNS schema to list all the DNS events from the last 24 hours that have a response code of ‘NXDOMAIN’ and were aggregated by the source IP address in 15-minute intervals. The solution must maximize query performance.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 6
You have a Microsoft 365 subscription that uses Microsoft 365 Defender.
A remediation action for an automated investigation quarantines a file across multiple devices.
You need to mark the file as safe and remove the file from quarantine on the devices.
What should you use in the Microsoft 365 Defender portal?
- From the History tab in the Action center, revert the actions.
- From the investigation page, review the AIR processes.
- From Quarantine from the Review page, modify the rules.
- From Threat tracker, review the queries.
Correct answer: A
Explanation:
A: 5 - Mosted A: 5 - Mosted
Question 7
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to validate that Microsoft Defender for Cloud will trigger an alert when a malicious file is present on an Azure virtual machine running Windows Server.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
Correct answer: To work with this question, an Exam Simulator is required.
Question 8
You have an Azure subscription that uses Microsoft Defender for Cloud.
You create a Google Cloud Platform (GCP) organization named GCP1.
You need to onboard GCP1 to Defender for Cloud by using the native cloud connector. The solution must ensure that all future GCP projects are onboarded automatically.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 9
You have an Azure subscription that has Microsoft Defender for Cloud enabled for all supported resource types.
You create an Azure logic app named LA1.
You plan to use LA1 to automatically remediate security risks detected in Defender for Cloud.
You need to test LA1 in Defender for Cloud.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 10
You have an Azure subscription that contains a virtual machine named VM1 and uses Microsoft Defender for Cloud.
Microsoft Defender for Cloud has automatic provisioning configured to use Azure Monitor Agent.
You need to create a custom alert suppression rule that will suppress false positive alerts for suspicious use of PowerShell on VM1.
What should you do first?
- From Microsoft Defender for Cloud, export the alerts to a Log Analytics workspace.
- From Microsoft Defender for Cloud, add a workflow automation.
- On VM1, trigger a PowerShell alert.
- On VM1, run the Get-MPThreatCatalog cmdlet.
Correct answer: C
Explanation:
C: 4 - Mosted C: 4 - Mosted
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files
HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files
ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!