Download Microsoft 365 Security Administration.MS-500.PracticeTest.2019-03-08.13q.tqb
| Vendor: | Microsoft |
| Exam Code: | MS-500 |
| Exam Name: | Microsoft 365 Security Administration |
| Date: | Mar 08, 2019 |
| File Size: | 193 KB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
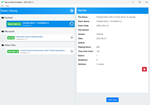
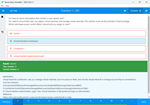
An administrator configures Azure AD Privileged Identity Management as shown in the following exhibit.
What should you do to meet the security requirements?
- Change the Assignment Type for Admin2 to Permanent
- From the Azure Active Directory admin center, assign the Exchange administrator role to Admin2
- From the Azure Active Directory admin center, remove the Exchange administrator role to Admin1
- Change the Assignment Type for Admin1 to Eligible
Correct answer: D
Question 2
You need to recommend a solution for the user administrators that meets the security requirements for auditing. Which blade should you recommend using from the Azure Active Directory admin center?
- Sign-ins
- Azure AD Identity Protection
- Authentication methods
- Access review
Correct answer: A
Question 3
An administrator configures Azure AD Privileged Identity Management as shown in the following exhibit:
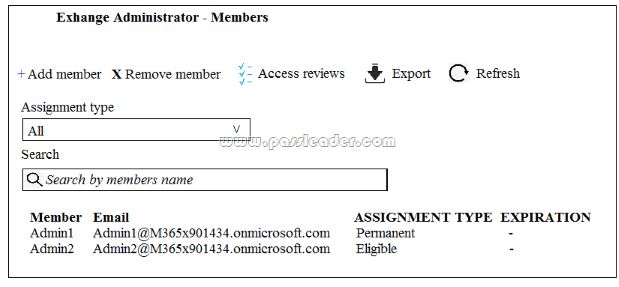
What should you do to meet the security requirements?
- Change the Assignment Type for Admin2 to Permanent.
- From the Azure Active Directory admin center, assign the Exchange administrator role to Admin2.
- From the Azure Active Directory admin center, remove the Exchange administrator role to Admin1.
- Change the Assignment Type for Admin1 to Eligible.
Correct answer: D
Question 4
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
- Source Anchor: objectGUID
- Password Hash Synchronization: Disabled
- Password writeback: Disabled
- Directory extension attribute sync: Disabled
- Azure AD app and attribute filtering: Disabled
- Exchange hybrid deployment: Disabled
- User writeback: Disabled
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection.
Solution: You modify the Password Hash Synchronization settings.
Does that meet the goal?
- Yes
- No
Correct answer: A
Question 5
You have a Microsoft 365 tenant. You create a label named CompanyConfidential in Microsoft Azure Information Protection. You add CompanyConfidential to a global policy. A user protects an email message by using CompanyConfidential and sends the label to several external recipients. The external recipients report that they cannot open the email message. You need to ensure that the external recipients can open protected email messages sent to them.
Solution: You modify the encryption settings of the label.
Does this meet the goal?
- Yes
- No
Correct answer: B
Question 6
You have a hybrid Microsoft 365 environment. All computers run Windows 10 and are managed by using Microsoft Intune. You need to create a Microsoft Azure Active Directory (Azure AD) conditional access policy that will allow only Windows 10 computers marked as compliant to establish a VPN connection to the on-premises network. What should you do first?
- From the Azure Active Directory admin center, create a new certificate.
- Enable Application Proxy in Azure AD.
- From Active Directory Administrative Center, create a Dynamic Access Control policy.
- From the Azure Active Directory admin center, configure authentication methods.
Correct answer: A
Question 7
You have a Microsoft 365 Enterprise E5 subscription. You use Windows Defender Advanced Threat Protection (Windows Defender ATP). You plan to use Microsoft Office 365 Attack simulator. What is a prerequisite for running Attack simulator?
- Enable multi-factor authentication (MFA)
- Configure Advanced Threat Protection (ATP)
- Create a Conditional Access App Control policy for accessing Office 365
- Integrate Office 365 Threat Intelligence and Windows Defender ATP
Correct answer: A
Question 8
Your company has 500 computers. You plan to protect the computers by using Windows Defender Advanced Threat Protection (Windows Defender ATP). Twenty of the computers belong to company executives. You need to recommend a remediation solution that meets the following requirements:
- Windows Defender ATP administrators must manually approve all remediation for the executives.
- Remediation must occur automatically for all other users.
What should you recommend doing from Windows Defender Security Center?
- Configure 20 system exclusions on automation allowed/block lists.
- Configure two alert notification rules.
- Download an offboarding package for the computers of the 20 executives.
- Create two machine groups.
Correct answer: D
Question 9
You have a Microsoft 365 subscription. You need to create data loss prevention (DLP) queries in Microsoft SharePoint Online to find sensitive data stored in sites. Which type of site collection should you create first?
- Records Center
- Compliance Policy Center
- eDiscovery Center
- Enterprise Search Center
- Document Center
Correct answer: C
Question 10
You have a Microsoft 365 subscription. You need to enable auditing for all Microsoft Exchange Online users. What should you do?
- From the Exchange admin center, create a journal rule.
- Run the Set-MailboxDatabase cmdlet.
- Run the Set-Mailbox cmdlet.
- From the Exchange admin center, create a mail flow message trace rule.
Correct answer: C
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files
HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files
ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!