Download Fortinet NSE 7 - OT Security 7.2.NSE7_OTS-7.2.ExamTopics.2025-09-25.36q.tqb
| Vendor: | Fortinet |
| Exam Code: | NSE7_OTS-7.2 |
| Exam Name: | Fortinet NSE 7 - OT Security 7.2 |
| Date: | Sep 25, 2025 |
| File Size: | 2 MB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
As an OT network administrator, you are managing three FortiGate devices that each protect different levels on the Purdue model. To increase traffic visibility, you are required to implement additional security measures to detect protocols from PLCs.
Which security sensor must you implement to detect protocols on the OT network?
- Antivirusinspection
- Intrusion prevention system (IPS)
- Application control
- Deep packet inspection (DPI)
Correct answer: C
Explanation:
B: 1C: 5 - Mosted B: 1C: 5 - Mosted
Question 2
Which two statements are true when you deploy FortiGate as an offline IDS? (Choose two.)
- Network traffic goes through FortiGate.
- Network attacks can be detected and blocked.
- FortiGate acts as network sensor.
- FortiGate receives traffic from configured port mirroring.
Correct answer: CD
Explanation:
CD: 1 CD: 1
Question 3
Refer to the exhibit.
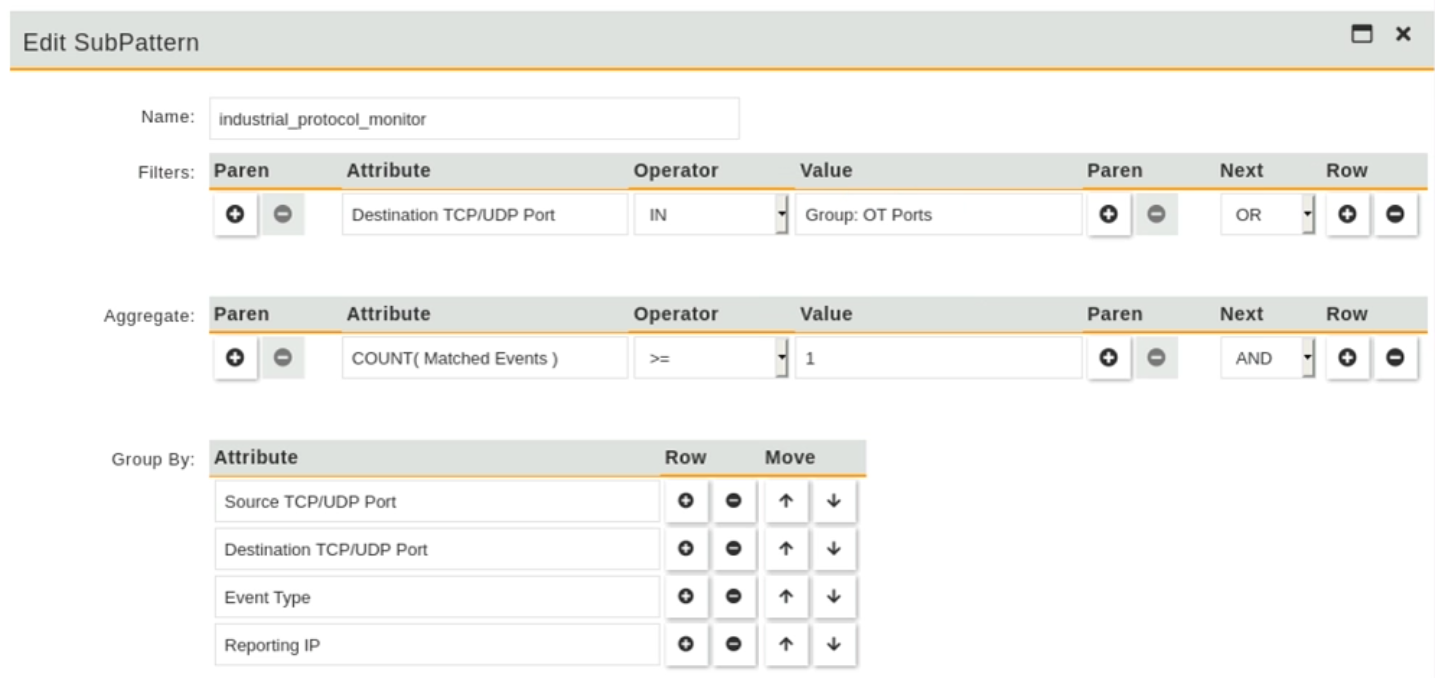
A new operational technology rule is being created to monitor Modbus protocol traffic on FortiSIEM.
Which action will ensure all Modbus messages on the network match the rule?
- Set the Aggregate attribute value to equal to or greater than zero.
- Add a new condition to filter Modbus traffic based on the Source TCP/UDP port.
- This rule is valid and requires no additional changes.
- Remove attributes in the Group By section that are not configured in the Filter section.
Correct answer: B
Explanation:
B: 1 B: 1
Question 4
Refer to the exhibit.
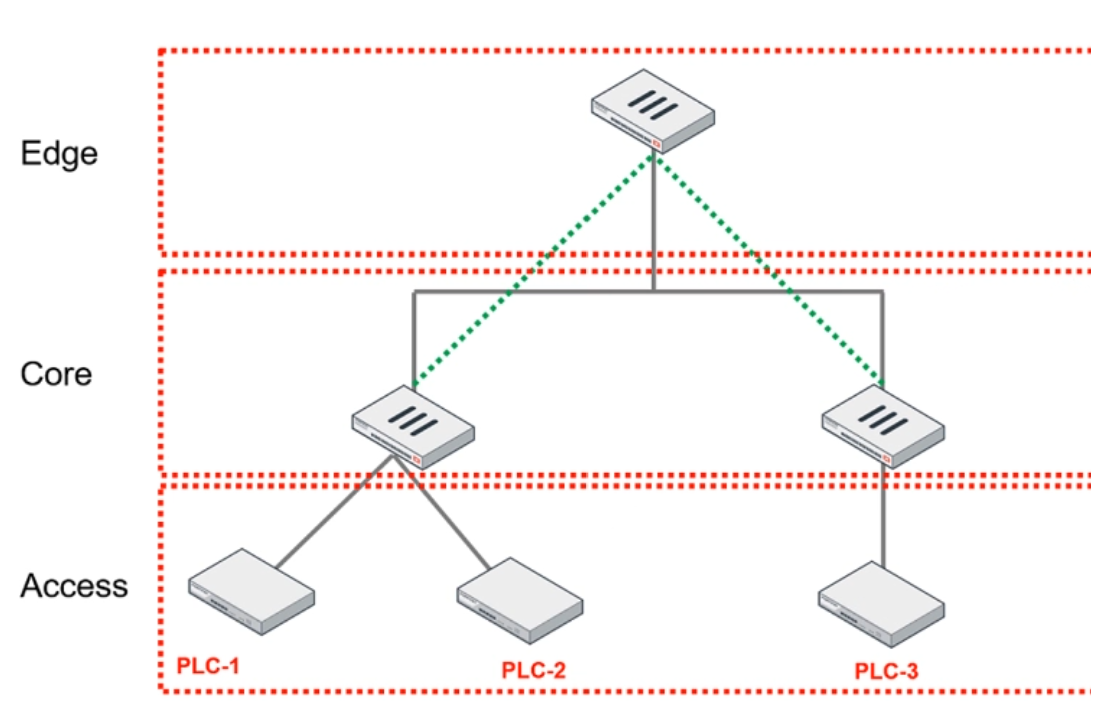
You are assigned to implement a remote authentication server in the OT network.
Which part of the hierarchy should the authentication server be part of?
- Edge
- Cloud
- Core
- Access
Correct answer: C
Explanation:
A: 2 - MostedC: 2 A: 2 - MostedC: 2
Question 5
Refer to the exhibit.
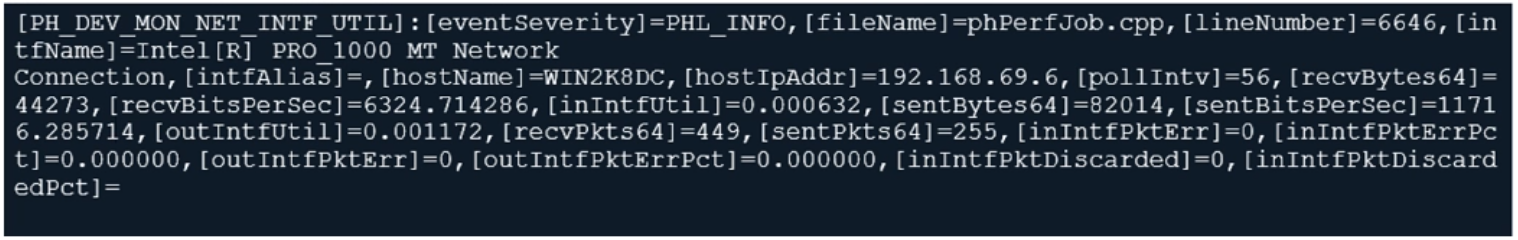
From your analysis of the output, which statement about the output is true?
- This is a sample of an SNMP temperature control event log.
- This is a sample of a FortiAnalyzer system interface event log.
- This is a sample of a PAM event type.
- This is a sample of FortiGate interface statistics.
Correct answer: D
Explanation:
C: 3 C: 3
Question 6
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
- Risk
- IPS
- List
- Security
- Overview
Correct answer: ACE
Explanation:
ACE: 1 ACE: 1
Question 7
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted for credentials during authentication.
What is a possible reason?
- Two-factor authentication is not configured with the RADIUS authentication method.
- The user was determined by the Security Fabric.
- FortiGate determined the user by passive authentication.
- FortiNAC determined the user by the DHCP fingerprint method.
Correct answer: C
Explanation:
C: 1 C: 1
Question 8
With the limit of using one firewall device, the administrator enables multi-VDOM on FortiGate to provide independent multiple security domains to each ICS network.
Which statement ensures security protection is in place for all ICS networks?
- Each traffic VDOM must have a direct connection to FortiGuard services to receive the required security updates.
- The management VDOM must have access to all global security services.
- Each VDOM must have an independent security license.
- Traffic between VDOMs must pass through the physical interfaces of FortiGate to check for security incidents.
Correct answer: B
Explanation:
B: 1 B: 1
Question 9
What are two critical tasks the OT network auditors must perform during OT network risk assessment and management? (Choose two.)
- Implementing strategies to automatically bring PLCs offline
- Planning a threat hunting strategy
- Creating disaster recovery plans to switch operations to a backup plant
- Evaluating what can go wrong before it happens
Correct answer: BD
Explanation:
BD: 1 BD: 1
Question 10
Which type of attack posed by skilled and malicious users of security level 3 (SL 3) of IEC 62443 is designed to defend against intentional attacks?
- Unintentional operator error
- Access to moderate resources
- Low access to resources
- Substantial resources
Correct answer: B
Explanation:
B: 1 B: 1
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files
HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files
ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!