Download Fortinet NSE 6 - FortiNAC 8.5.NSE6_FNC-8.5.ExamTopics.2025-10-08.30q.vcex
| Vendor: | Fortinet |
| Exam Code: | NSE6_FNC-8.5 |
| Exam Name: | Fortinet NSE 6 - FortiNAC 8.5 |
| Date: | Oct 08, 2025 |
| File Size: | 192 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
What agent is required in order to detect an added USB drive?
- Mobile
- Passive
- Dissolvable
- Persistent
Correct answer: D
Explanation:
Expand the Persistent Agent folder. Select USB Detection from the tree.Reference:https://docs.fortinet.com/document/fortinac/8.5.2/administration-guide/814147/usb-detection Expand the Persistent Agent folder. Select USB Detection from the tree.
Reference:
https://docs.fortinet.com/document/fortinac/8.5.2/administration-guide/814147/usb-detection
Question 2
How should you configure MAC notification traps on a supported switch?
- Configure them only on ports set as 802.1q trunks
- Configure them on all ports except uplink ports
- Configure them on all ports on the switch
- Configure them only after you configure linkup and linkdown traps
Correct answer: B
Explanation:
Configure SNMP MAC Notification traps on all access ports (do not include uplinks).Reference:https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/be7fcde9-9685-11e9-81a4-00505692583a/Configuring_Traps_for_MAC_Notification.pdf Configure SNMP MAC Notification traps on all access ports (do not include uplinks).
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/be7fcde9-9685-11e9-81a4-00505692583a/Configuring_Traps_for_MAC_Notification.pdf
Question 3
In a wireless integration, how does FortiNAC obtain connecting MAC address information?
- Link traps
- End station traffic monitoring
- MAC notification traps
- RADIUS
Correct answer: D
Explanation:
D: 1 - MostedIntelligent Access Points (IAPs) and controllers support two methods of RADIUS based authentication: RADIUS MAC authentication and 802.1x authentication.Reference:https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/9019f7f8-200d-11e9-b6f6-f8bc1258b856/FortiNAC_Wireless_Integration_Overview.pdf D: 1 - Mosted
Intelligent Access Points (IAPs) and controllers support two methods of RADIUS based authentication: RADIUS MAC authentication and 802.1x authentication.
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/9019f7f8-200d-11e9-b6f6-f8bc1258b856/FortiNAC_Wireless_Integration_Overview.pdf
Question 4
Which system group will force at-risk hosts into the quarantine network, based on point of connection?
- Forced Quarantine
- Forced Remediation
- Forced Isolation
- Physical Address Filtering
Correct answer: B
Explanation:
A: 2B: 3 - Mosted A: 2B: 3 - Mosted
Question 5
Which command line shell and scripting language does FortiNAC use for WinRM?
- Powershell
- Bash
- Linux
- DOS
Correct answer: A
Explanation:
A: 2 - MostedOpen Windows PowerShell or a command prompt. Run the following command to determine if you already have WinRM over HTTPS configured.Reference:https://docs.fortinet.com/document/fortinac/8.7.0/administration-guide/246310/winrm-device-profile-requirements-and-setup A: 2 - Mosted
Open Windows PowerShell or a command prompt. Run the following command to determine if you already have WinRM over HTTPS configured.
Reference:
https://docs.fortinet.com/document/fortinac/8.7.0/administration-guide/246310/winrm-device-profile-requirements-and-setup
Question 6
What causes a host's state to change to "at risk"?
- The host has been administratively disabled.
- The logged on user is not found in the Active Directory.
- The host has failed an endpoint compliance policy or admin scan.
- The host is not in the Registered Hosts group.
Correct answer: C
Explanation:
C: 2 - MostedFailure ג€" Indicates that the host has failed the scan. This option can also be set manually. When the status is set to Failure the host is marked "At Risk" for the selected scan.Reference:https://docs.fortinet.com/document/fortinac/8.3.0/administration-guide/241168/host-health-and-scanning C: 2 - Mosted
Failure ג€" Indicates that the host has failed the scan. This option can also be set manually. When the status is set to Failure the host is marked "At Risk" for the selected scan.
Reference:
https://docs.fortinet.com/document/fortinac/8.3.0/administration-guide/241168/host-health-and-scanning
Question 7
In which view would you find who made modifications to a Group?
- The Admin Auditing view
- The Alarms view
- The Event Management view
- The Security Events view
Correct answer: A
Explanation:
A: 1 - MostedIt's important to audit Group Policy changes in order to determine the details of changes made to Group Policies by delegated users.Reference:https://www.lepide.com/how-to/audit-chnages-made-to-group-policy-objects.html A: 1 - Mosted
It's important to audit Group Policy changes in order to determine the details of changes made to Group Policies by delegated users.
Reference:
https://www.lepide.com/how-to/audit-chnages-made-to-group-policy-objects.html
Question 8
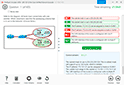
Refer to the exhibit, and then answer the question below.
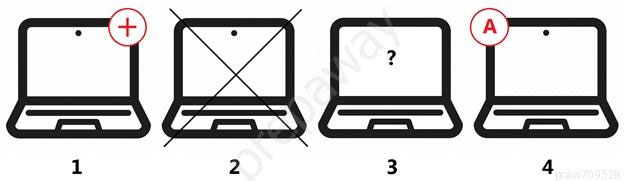
Which host is rogue?
- 4
- 2
- 3
- 1
Correct answer: C
Explanation:
C: 1Reference:https://docs.fortinet.com/document/fortinac/8.6.0/administration-guide/283146/evaluating-rogue-hosts C: 1
Reference:
https://docs.fortinet.com/document/fortinac/8.6.0/administration-guide/283146/evaluating-rogue-hosts
Question 9
In an isolation VLAN, which three services does FortiNAC supply? (Choose three.)
- DNS
- NTP
- SMTP
- DHCP
- Web
Correct answer: ADE
Explanation:
ADE: 1Reference:https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/8bec453a-b242-11e9-a989-00505692583a/AdminGuide-860-PDF.pdf ADE: 1
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/8bec453a-b242-11e9-a989-00505692583a/AdminGuide-860-PDF.pdf
Question 10
Which three communication methods are used by the FortiNAC to gather information from, and control, infrastructure devices? (Choose three.)
- SNMP
- RADIUS
- FTP
- CLI
- SMTP
Correct answer: ABD
Explanation:
ABD: 5 - Mosted ABD: 5 - Mosted
Question 11
Which connecting endpoints are evaluated against all enabled device profiling rules?
- Known trusted devices each time they change location
- Rogues devices, each time they connect
- Rogues devices, only when they connect for the first time
- All hosts, each time they connect
Correct answer: A
Explanation:
C: 1 - MostedFortiNAC process to classify rogue devices and create an organized inventory of known trusted registered devices.Reference:https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/9529d49c-892c-11e9-81a4-00505692583a/FortiNAC_Device_Profiler_Configuration.pdf C: 1 - Mosted
FortiNAC process to classify rogue devices and create an organized inventory of known trusted registered devices.
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/9529d49c-892c-11e9-81a4-00505692583a/FortiNAC_Device_Profiler_Configuration.pdf
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files
HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files
ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!