Download Fortinet NSE 6 -FortiMail 7-2.NSE6_FML-7.2.ExamTopics.2025-11-07.28q.tqb
| Vendor: | Fortinet |
| Exam Code: | NSE6_FML-7.2 |
| Exam Name: | Fortinet NSE 6 -FortiMail 7-2 |
| Date: | Nov 07, 2025 |
| File Size: | 3 MB |
How to open TQB files?
Files with TQB (Taurus Question Bank) extension can be opened by Taurus Exam Studio.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
Refer to the exhibits showing SMTP limits (Session Profile — SMTP Limits), and domain settings (Domain Settings, and Domain Settings — Other) of a FortiMail device.
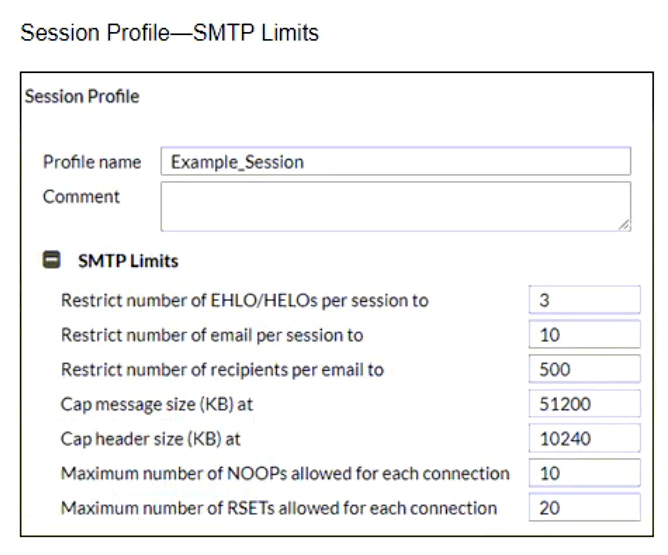
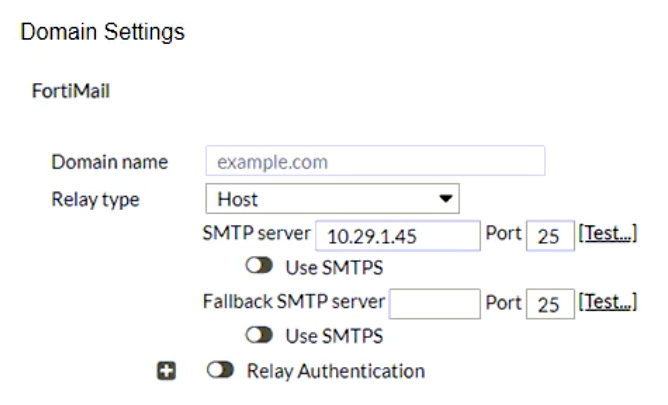
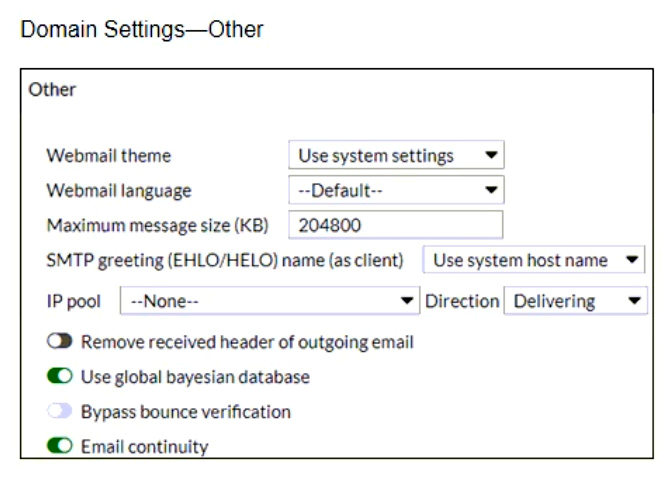
Which message size limit in KB will the FortiMail apply to outbound email?
- 204800
- There is no message size limit for outbound email from a protected domain.
- 10240
- 51200
Correct answer: D
Explanation:
A: 1D: 1 - Mosted A: 1D: 1 - Mosted
Question 2
A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
- MAIL FROM: [email protected] RCPT TO: [email protected]
- MAIL FROM: [email protected] RCPT TO: [email protected]
- MAIL FROM: [email protected] RCPT TO: [email protected]
- MAIL FROM: [email protected] RCPT TO: [email protected]
Correct answer: AB
Explanation:
CD: 2 - Mosted CD: 2 - Mosted
Question 3
Refer to the exhibit, which shows a topology diagram of two separate email domains.
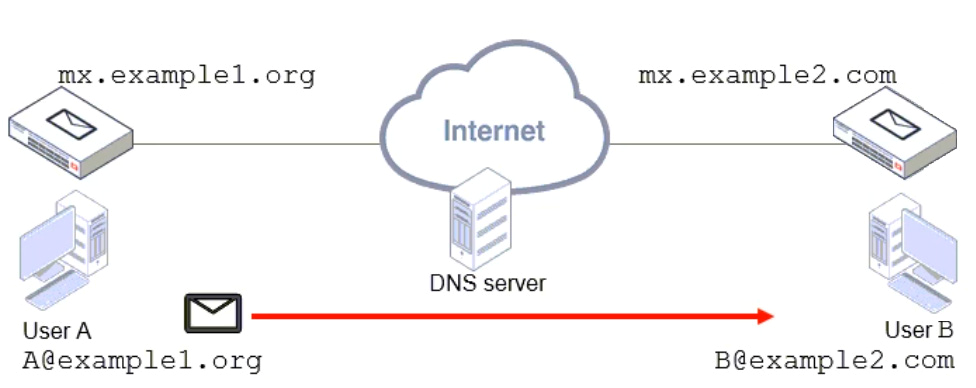
Which two statements correctly describe how an email message is delivered from User A to User B? (Choose two.)
- mx.example1.org will forward the email message to the MX record that has the lowest preference.
- User B will retrieve the email message using either POP3 or IMAP.
- User A’s MUA will perform a DNS MX record lookup to send the email message.
- The DNS server will act as an intermediary MTA.
Correct answer: AB
Question 4
Refer to the exhibit which shows the output of an email transmission using a telnet session.
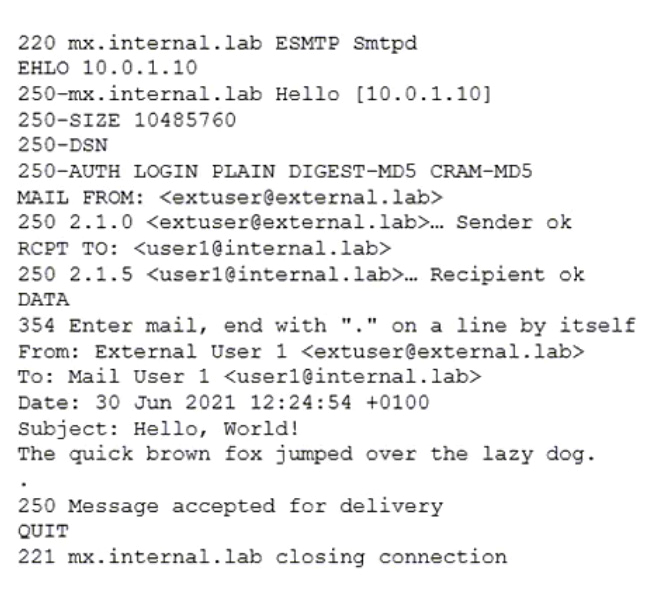
What are two correct observations about this SMTP session? (Choose two.)
- The SMTP envelope addresses are different from the message header addresses.
- The "250 Message accepted for delivery" message is part of the message body.
- The "Subject" is part of the message header.
- The "220 mx.internal.lab ESMTP Smtpd" message is part of the SMTP banner.
Correct answer: CD
Question 5
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
- Policy configuration changes of all cluster members from the primary device.
- Mail statistics of all cluster members on the primary device.
- Cross-device log searches across all cluster members from the primary device.
- Firmware update of all cluster members from the primary device.
Correct answer: BC
Question 6
Refer to the exhibit which shows a command prompt output of a telnet command.
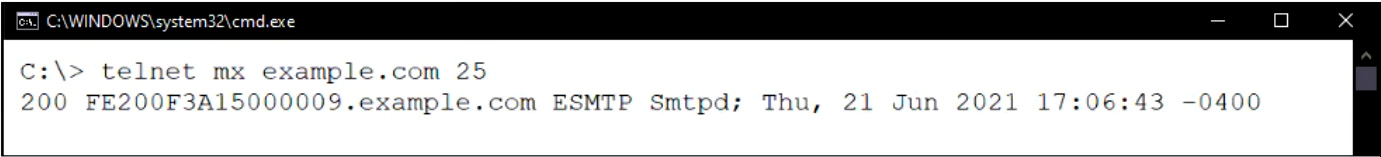
Which configuration change must you make to prevent the banner from displaying the FortiMail serial number?
- Change the host name
- Add a protected domain
- Configure a local domain name
- Change the operation mode
Correct answer: A
Question 7
Refer to the exhibits which shows a DLP scan profile configuration (DLP Scan Rule 1 and DLP Scan Rule 2) from a FortiMail device.
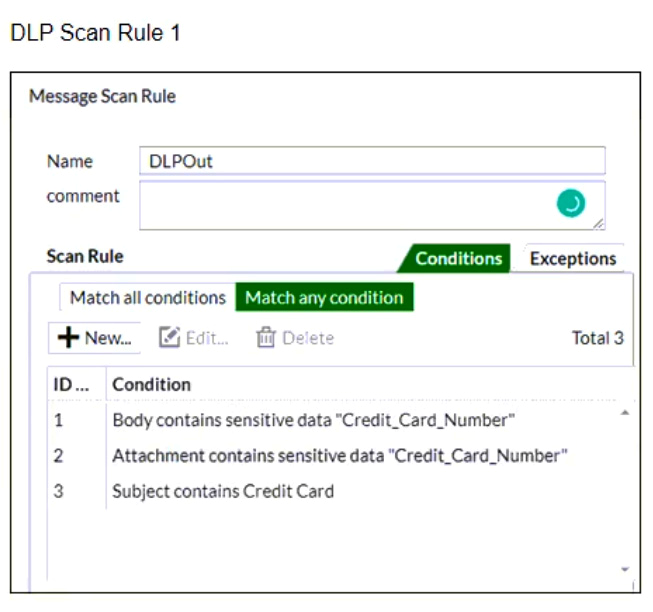
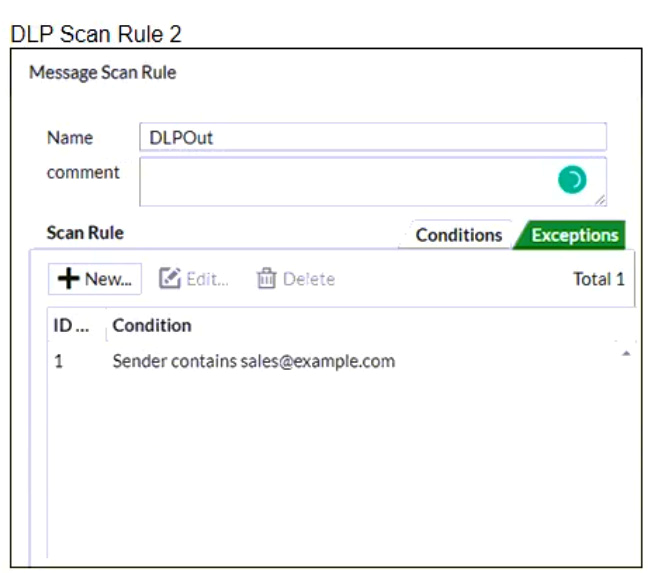
Which two message types will trigger this DLP scan rule? (Choose two.)
- An email that contains credit card numbers in the body, attachment, and subject will trigger this scan rule.
- An email sent from [email protected] will trigger this scan rule, even without matching any conditions.
- An email message with a subject that contains the term “credit card” will trigger this scan rule.
- An email message that contains credit card numbers in the body will trigger this scan rule.
Correct answer: CD
Question 8
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks. What option can the administrator configure to prevent these types of attacks?
- Impersonation analysis
- Dictionary profile with predefined smart identifiers
- Bounce tag verification
- Content disarm and reconstruction
Correct answer: A
Question 9
A FortiMail is configured with the protected domain example.com.
On this FortiMail, which two envelope addresses are considered incoming? (Choose two.)
- MAIL FROM: [email protected] RCPT TO: [email protected]
- MAIL FROM: [email protected] RCPT TO: [email protected]
- MAIL FROM: [email protected] RCPT TO: [email protected]
- MAIL FROM: [email protected] RCPT TO: [email protected]
Correct answer: AC
Question 10
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
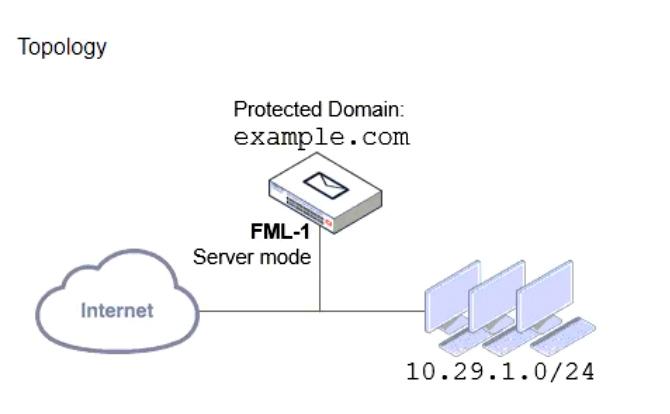
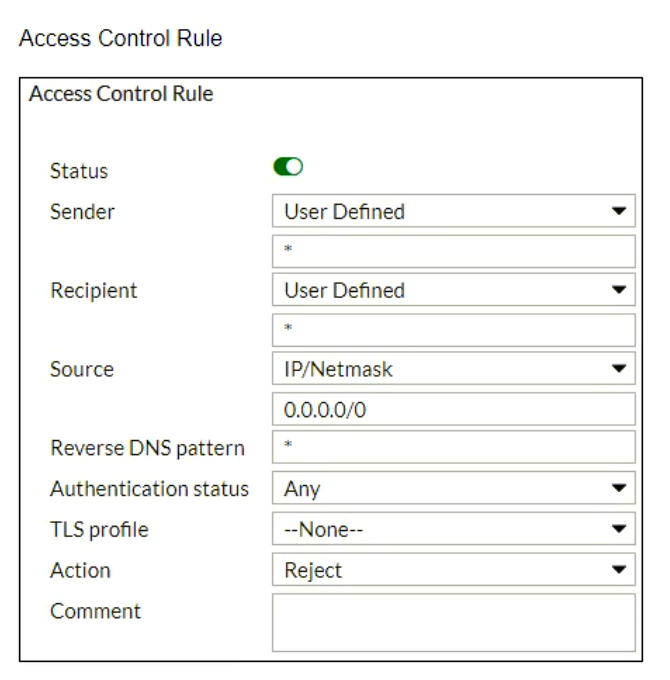
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)
- The Sender IP/netmask should be set to 10.29.1.0/24.
- The Action should be set to Reject.
- The Recipient pattern should be set to *@example.com.
- The Authentication status should be set to Authenticated.
Correct answer: AD
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files
HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files
ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!