Download FCSS-Security Operations 7.4 Analyst.FCSS_SOC_AN-7.4.ExamTopics.2025-10-08.24q.vcex
| Vendor: | Fortinet |
| Exam Code: | FCSS_SOC_AN-7.4 |
| Exam Name: | FCSS-Security Operations 7.4 Analyst |
| Date: | Oct 08, 2025 |
| File Size: | 3 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Purchase
Coupon: TAURUSSIM_20OFF
Discount: 20%
Demo Questions
Question 1
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three.)
- Web filter logs
- Email filter logs
- DNS filter logs
- Application filter logs
- IPS logs
Correct answer: BDE
Explanation:
ACE: 1 - Mosted ACE: 1 - Mosted
Question 2
Refer to the exhibit.
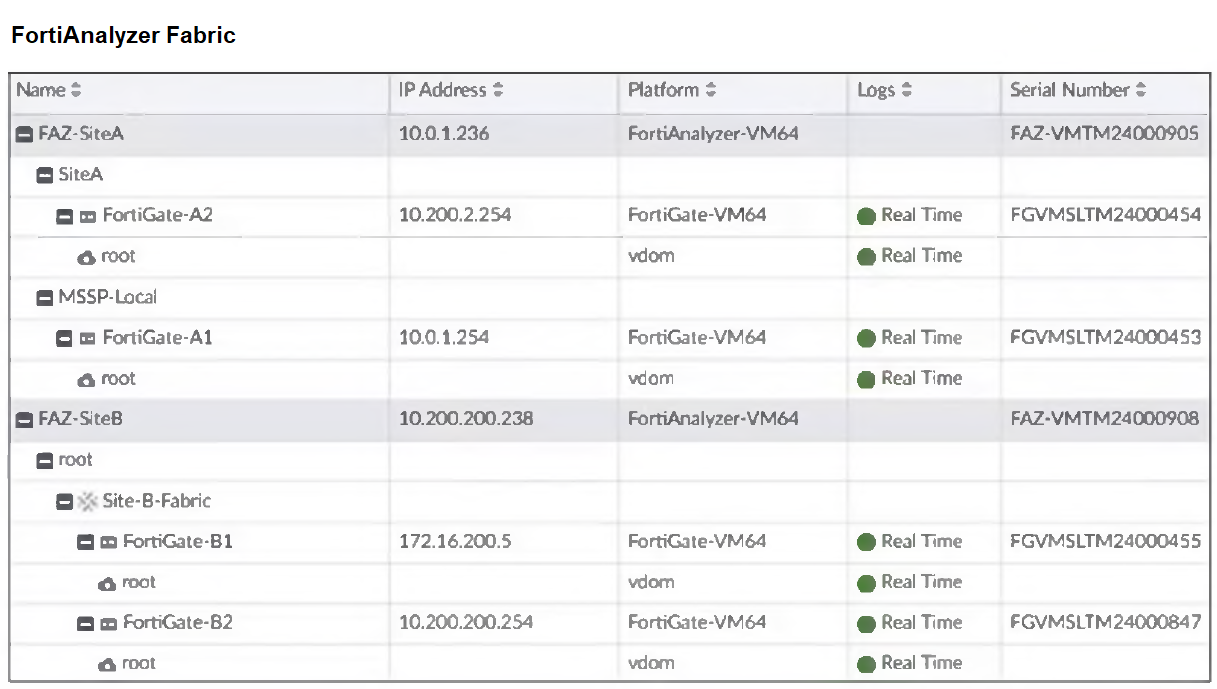
Assume that all devices in the FortiAnalyzer Fabric are shown in the image.
Which two statements about the FortiAnalyzer Fabric deployment are true? (Choose two.)
- FortiGate-B1 and FortiGate-B2 are in a Security Fabric.
- There is no collector in the topology.
- All FortiGate devices are directly registered to the supervisor.
- FAZ-SiteA has two ADOMs enabled.
Correct answer: BD
Explanation:
AD: 1 - Mosted AD: 1 - Mosted
Question 3
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
- The supervisor uses an API to store logs, incidents, and events locally.
- Downstream collectors can forward logs to Fabric members.
- Logging devices must be registered to the supervisor.
- Fabric members must be in analyzer mode.
Correct answer: AD
Explanation:
BD: 2 - Mosted BD: 2 - Mosted
Question 4
Which two ways can you create an incident on FortiAnalyzer? (Choose two.)
- Using a custom event handler
- Using a connector action
- By running a playbook
- Manually, on the Event Monitor page
Correct answer: AD
Explanation:
CD: 2 - Mosted CD: 2 - Mosted
Question 5
According to the National Institute of Standards and Technology (NIST) cybersecurity framework, incident handling activities can be divided into phases.
In which incident handling phase do you quarantine a compromised host in order to prevent an adversary from using it as a stepping stone to the next phase of an attack?
- Containment
- Recovery
- Analysis
- Eradication
Correct answer: A
Explanation:
A: 1 A: 1
Question 6
Refer to the exhibit.
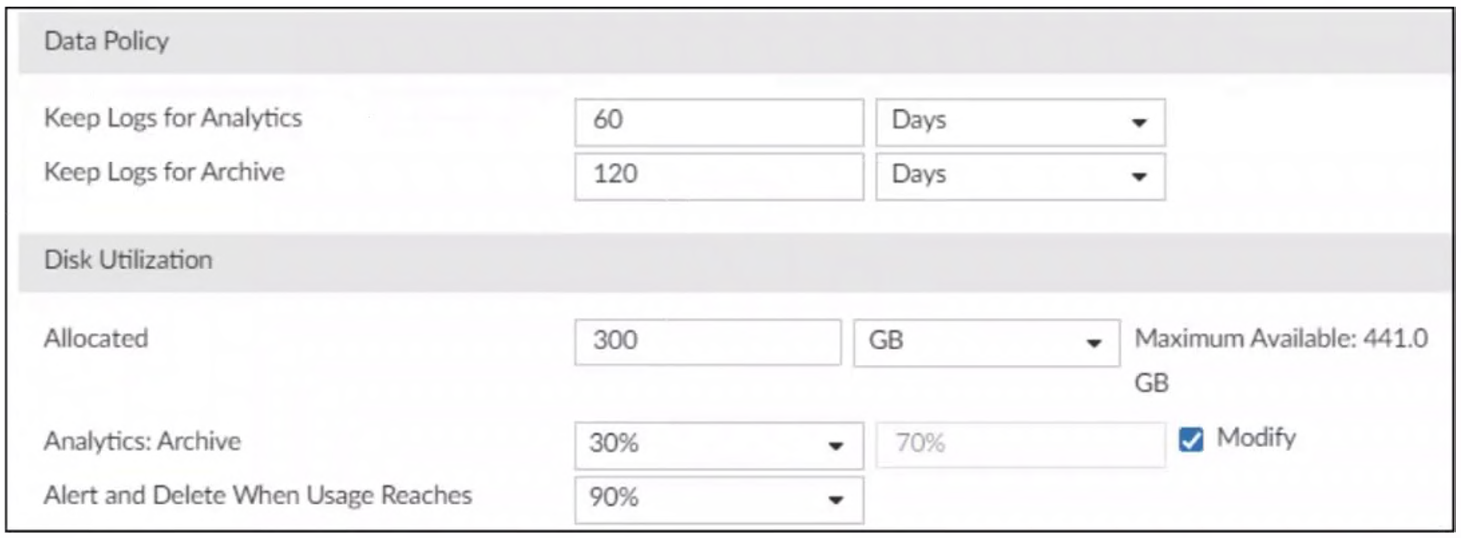
You are tasked with reviewing a new FortiAnalyzer deployment in a network with multiple registered logging devices. There is only one FortiAnalyzer in the topology.
Which potential problem do you observe?
- The archive retention period is too long.
- The analytics-to-archive ratio is misconfigured.
- The disk space allocated is insufficient.
- The analytics retention period is too long.
Correct answer: B
Explanation:
B: 1 B: 1
Question 7
Which FortiAnalyzer feature uses the SIEM database for advance log analytics and monitoring?
- Threat hunting
- Asset Identity Center
- Outbreak alerts
- Event monitor
Correct answer: A
Explanation:
A: 1 A: 1
Question 8
Which statement describes automation stitch integration between FortiGate and FortiAnalyzer?
- An automation stitch is configured on FortiAnalyzer and mapped to FortiGate using the FortiOS connector.
- An event handler on FortiAnalyzer is configured to send a notification to FortiGate to trigger an automation stitch.
- A security profile on FortiGate triggers a violation and FortiGate sends a webhook call to FortiAnalyzer.
- An event handler on FortiAnalyzer executes an automation stitch when an event is created.
Correct answer: B
Explanation:
B: 1 B: 1
Question 9
Refer to the exhibits.
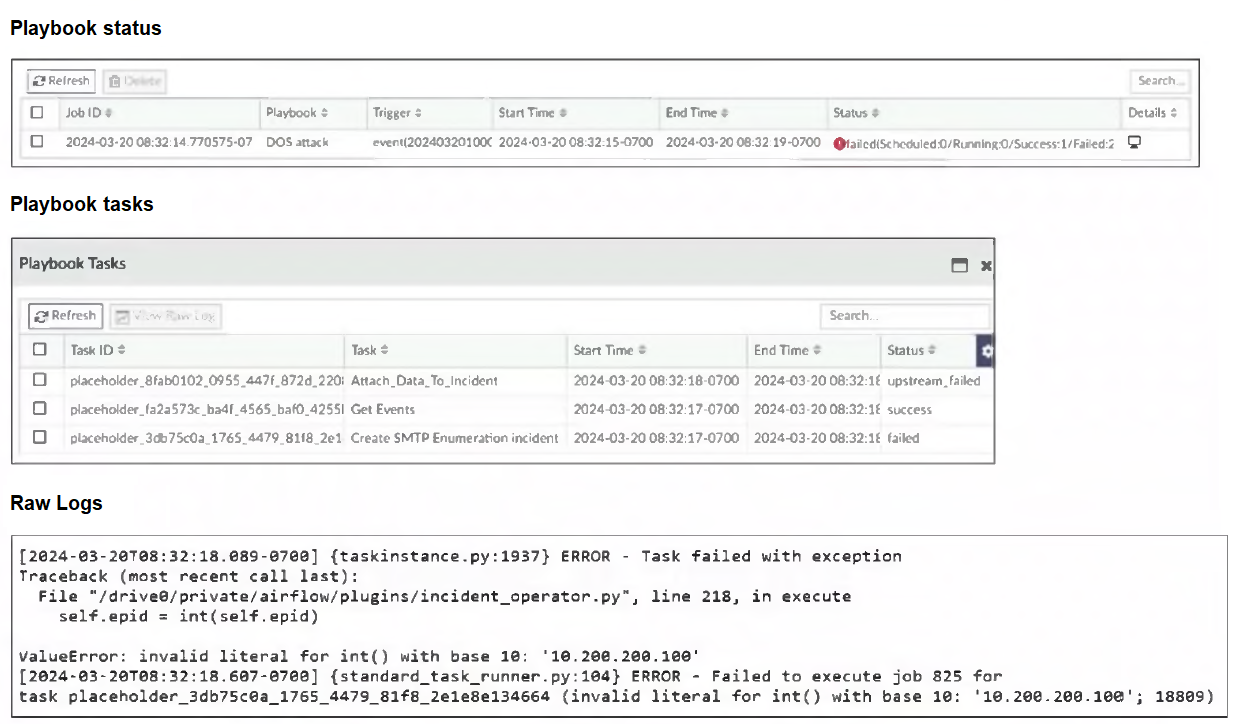
The DOS attack playbook is configured to create an incident when an event handler generates a denial-of-service (DoS) attack event.
Why did the DOS attack playbook fail to execute?
- The Attach_Data_To_Incident task is expecting an integer value but is receiving the incorrect data type.
- The Get Events task is configured to execute in the incorrect order.
- The Attach_Data_To_Incident task failed.
- The Create SMTP Enumeration incident task is expecting an integer value but is receiving the incorrect data type.
Correct answer: D
Explanation:
B: 2 B: 2
Question 10
Which two types of variables can you use in playbook tasks? (Choose two.)
- Output
- Input
- Create
- Trigger
Correct answer: AD
Explanation:
AD: 1 AD: 1
Question 11
Which statement best describes the MITRE ATT&CK framework?
- It describes attack vectors targeting network devices and servers, but not user endpoints.
- It provides a high-level description of common adversary activities, but lacks technical details.
- It covers tactics, techniques, and procedures, but does not provide information about mitigations.
- It contains some techniques or subtechniques that fall under more than one tactic.
Correct answer: D
Explanation:
D: 1 D: 1
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files
HOW TO OPEN VCEX FILES
Use ProfExam Simulator to open VCEX files
ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!